Automated governance, simplified
Trusted partner to security-first companies
.png?width=225&height=60&name=Mask%20group%20(64).png)






Why Privacy Teams and Data Owners Need This
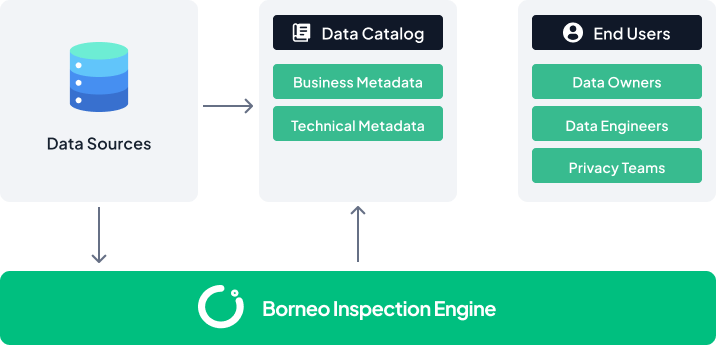
Instant Visibility into Data Risks
Empower Data Owners
Smart Context for Smarter Decisions
How Borneo Transforms Data Governance
Privacy Teams
Can shift unscalable compliance tasks to data owners, saving thousands of hours on remediation.
Data Engineers
Can design and build better data catalogs for data scientists, reducing manual labeling efforts.
Data Owners
Can govern their sensitive data and document business use-cases and risks, enabling better data-driven business decisions.

Intelligent Automation for Seamless Data Governance
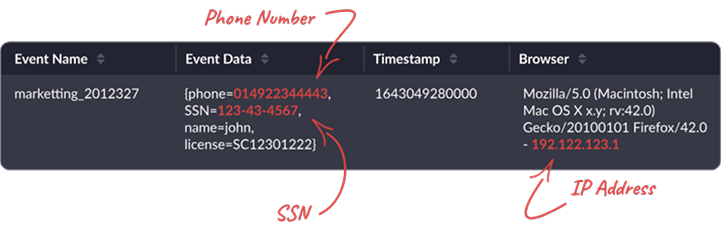
Identifies Complex Data
Only scanning for column labels is not enough. Sensitive data hides in all types of data structures. The example above shows SSN hiding in a JSON.
Automated Table Monitoring
Detects new or deleted tables automatically and performs scans without the need for manual automation.
Comprehensive Inspections
Conducts data-level inspections for more thorough sensitive data detection.
Our deployment model is designed keeping you in mind

Easy and Flexible Deployment
The deployment process takes ~10 minutes for SaaS and ~60 minutes for Private SaaS. No manual configuration. Start seeing results in a jiffy. Blazing fast time-to-value
Remain in Full Control of your Data
Private deployments ensure your data never leaves your cloud environment. Agent-less connectors and no-code integrations ensure seamless functionality without compromising data privacy.
No Management Overheads
Borneo requires minimal setup and configuration. No need for ongoing maintenance or dedicated teams to manage the platform— automatic updates, scaling, and monitoring.
Scales Efficiently
Borneo is built to handle petabyte-scale data seamlessly. With predictable infrastructure costs and efficient resource usage, you can scale confidently without surprises on your cloud bill.
Complements Your Data Stack
Seamlessly integrates with your existing tools and workflows to enhance. With agent-less connectors and no-code integrations, setup is simple and requires no changes to your existing infrastructure.
“Borneo solves the data visibility and proactive privacy management problem, allowing for confident security-informed decision making, visibility and proactive remediation across the enterprise.
Chris McCann, CISO, Chainlink,
Advisor, Borneo
.png?width=302&height=279&name=Mask%20group%20(2).png)
“Borneo provides us with real-time data security along with privacy data intelligence so our data teams can keep innovating without worrying about data leaks, misuse, or mishandling.
Himanshu Jha, Lead - Data Analytics and Data Science,
Circles.Life
.jpg?width=592&height=592&name=Picsart_24-12-20_18-13-52-602%20(1).jpg)
“We are always looking for innovative security products that can scale as we grow and don’t require constant babysitting. My team could deploy Borneo with ease and show instant value in 30 mins.
Shreyas Kumar, CISO,
Deserve
